MALWARE
Cybercriminals, state-sponsored hackers, and spies use advanced attacks that blend multiple tactics – such as spear phishing emails and malware – to penetrate organizations and steal sensitive data. Unaware that malware has infected their device; legitimate users become a conduit for these groups to access your networks and sensitive data.
Type of malware :
SPYWARE

RANSOMEWARE
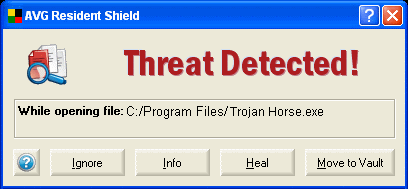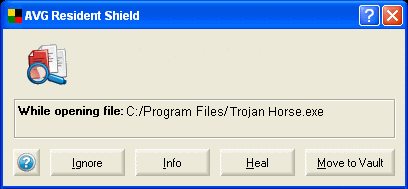
TROJANHORSE
WORM

Countermeasure
Enable firewall protection and Install Antivirus.